Opentape authorization vulnerability
Opentape is a web application to create a playlist of MP3 files that users can play on a web page. It was first released in 2008, just after the music service Muxtape stopped its services.
Opentape has a public view that is just a list of songs, and it has an admin part that can be used to upload songs and configure some things. The admin part is protected with a password, and if you try to access the admin part without logging in you are redirected to the login page. This is done with the following code, that is located at the start of the admin pages:
if (!is_logged_in()) {
header("Location: " . $REL_PATH . "code/login.php");
}
As you can see, it redirects the user to the login page, but it does not stop executing the rest of the script. This means that if we ignore the location header, we can access the admin part as if we were logged in.
Ignoring the location header
Burp Suite has an option to change responses that pass through its proxy. It’s located under “Match and Replace” in the “Options” tab of the proxy. Here, we can specify that we want to remove all location headers:
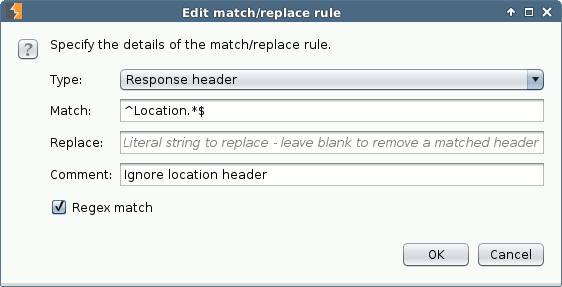
We remove all location headers in the responses. This way, we can access the protected section of Opentape without logging in.
I notified the developers of Opentape and made a pull request to fix this issue.





